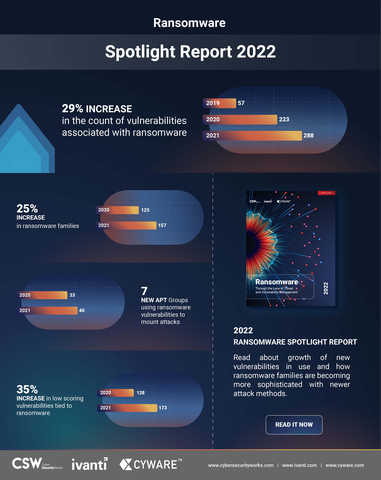
The report also revealed a 29% increase in CVEs associated with ransomware and a 26% increase in ransomware families in 2021 compared to the previous year
Ivanti, the provider of the Ivanti Neurons automation platform that discovers, manages, secures, and services IT assets from cloud to edge, today announced the results of the Ransomware Spotlight Year End Report that it conducted with Cyber Security Works, a Certifying Numbering Authority (CNA), and Cyware, the leading provider of Cyber Fusion, next-generation SOAR and threat intelligence solutions. The report identified 32 new ransomware families in 2021, bringing the total to 157 and representing a 26% increase over the previous year.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20220126005014/en/
Ransomware 2021 Year End Report Reveals Hackers are Increasingly Targeting Zero-Day Vulnerabilities and Supply Chain Networks for Maximum Impact (Graphic: Business Wire)
The report also found that these ransomware groups are continuing to target unpatched vulnerabilities and weaponize zero-day vulnerabilities in record time to instigate crippling attacks. At the same time, they are broadening their attack spheres and finding newer ways to compromise organizational networks and fearlessly trigger high-impact assaults.
Below are a few top observations and trends from the Ransomware Spotlight Year End Report:
- Unpatched vulnerabilities remain the most prominent attack vectors exploited by ransomware groups. The analysis uncovered 65 new vulnerabilities tied to ransomware last year, representing a 29% growth compared to the previous year and bringing the total number of vulnerabilities associated with ransomware to 288. Alarmingly, over one-third (37%) of these newly added vulnerabilities were actively trending on the dark web and repeatedly exploited. Parallelly, 56% of the 223 older vulnerabilities identified prior to 2021 continued to be actively exploited by ransomware groups. This proves that organizations need to prioritize and patch the weaponized vulnerabilities that ransomware groups are targeting – whether they are newly identified vulnerabilities or older vulnerabilities.
- Ransomware groups continue to find and leverage zero-day vulnerabilities, even before the CVEs are added to the National Vulnerability Database and patches are released. The QNAP (CVE-2021-28799), Sonic Wall (CVE-2021-20016), Kaseya (CVE-2021-30116), and most recently Apache Log4j (CVE-2021-44228) vulnerabilities were exploited even before they made it to the National Vulnerability Database (NVD). This dangerous trend highlights the need for agility from vendors in disclosing vulnerabilities and releasing patches based on priority. It also highlights the need for organizations to look beyond the NVD and keep an eye out for vulnerability trends, exploitation instances, vendor advisories, and alerts from security agencies while prioritizing the vulnerabilities to patch.
- Ransomware groups are increasingly targeting supply chain networks to inflict major damage and cause widespread chaos. A single supply chain compromise can open multiple avenues for threat actors to hijack complete system distributions across hundreds of victim networks. Last year, threat actors compromised supply chain networks via third-party applications, vendor-specific products, and open-source libraries. For example, the REvil group went after CVE-2021-30116 in the Kaseya VSA remote management service, launching a malicious update package that compromised all customers using onsite and remote versions of the VSA platform.
- Ransomware groups are increasingly sharing their services with others, much like legitimate SaaS offerings. Ransomware-as-a-service is a business model in which ransomware developers offer their services, variants, kits, or code to other malicious actors in return for payment. Exploit-as-a-service solutions allow threat actors to rent zero-day exploits from developers. Additionally, dropper-as-a-service allows newbie threat actors to distribute malware through programs that, when run, can execute a malicious payload onto a victim’s computer. And trojan-as-a-service, also called malware-as-a-service, enables anyone with an internet connection to obtain and deploy customized malware in the cloud, with zero installation.
With 157 ransomware families exploiting 288 vulnerabilities, ransomware groups are poised to wage rampant attacks in the coming years. And according to Coveware, organizations pay an average of $220,298 and suffer 23 days of downtime following a ransomware attack. This calls for an increased emphasis on cyber hygiene. Looking ahead, automating cyber hygiene will become increasingly important, especially as environments continue to get more complicated.
Srinivas Mukkamala, Senior Vice President of Security Products at Ivanti, said: “Ransomware groups are becoming more sophisticated, and their attacks more impactful. These threat actors are increasingly leveraging automated tool kits to exploit vulnerabilities and penetrate deeper into compromised networks. They are also expanding their targets and waging more attacks on critical sectors, disrupting daily lives and causing unprecedented damage. Organizations need to be extra vigilant and patch weaponized vulnerabilities without delays. This requires leveraging a combination of risk-based vulnerability prioritization and automated patch intelligence to identify and prioritize vulnerability weaknesses and then accelerate remediation.”
Anuj Goel, CEO at Cyware, said, “The substantive change we’ve observed across the ransomware landscape is that the attackers are looking to penetrate processes like patch deployment as much as they look for gaps in protection to penetrate systems. Vulnerability discovery must be met with an action that treats vulnerability data as intelligence to drive swift response decisions. As ransomware gangs operationalize their tooling, methods and target lists, it’s essential for SecOps teams to automate processes to self-heal vulnerable assets and systems to mitigate risk through real-time intelligence operationalization.”
Aaron Sandeen, CEO of Cyber Security Works, said, “Ransomware is devastating to customers and employees in every sector! In 2022, we will continue to see an increase in new vulnerabilities, exploit types, APT groups, ransomware families, CWE categories, and how old vulnerabilities are leveraged to exploit organizations. Leaders need innovative and predictive help to prioritize and remediate ransomware threats.”
The Ransomware Index Spotlight Report is based on data gathered from a variety of sources, including proprietary data from Ivanti and CSW, publicly available threat databases, and threat researchers and penetration testing teams. Click here to read the full report.
About Ivanti
Ivanti makes the Everywhere Workplace possible. In the Everywhere Workplace, employees use myriad devices to access IT applications and data over various networks to stay productive as they work from anywhere. The Ivanti Neurons automation platform connects the company’s industry-leading unified endpoint management, zero-trust security, and enterprise service management solutions, providing a unified IT platform that enables devices to self-heal and self-secure and empowers users to self-service. Over 40,000 customers, including 96 of the Fortune 100, have chosen Ivanti to discover, manage, secure, and service their IT assets from cloud to edge, and deliver excellent end-user experiences for employees, wherever and however they work. For more information, visit www.ivanti.com and follow @GoIvanti.
About Cyware
Cyware helps enterprise cybersecurity teams build platform-agnostic virtual cyber fusion centers. Cyware is transforming security operations by delivering the cybersecurity industry's only Virtual Cyber Fusion Center Platform with next-generation SOAR (security orchestration, automation, and response) technology. As a result, organizations can increase speed and accuracy while reducing costs and analyst burnout. Cyware's Virtual Cyber Fusion solutions make secure collaboration, information sharing, and enhanced threat visibility a reality for enterprises, sharing communities (ISAC/ISAO), MSSPs, and government agencies of all sizes and needs. https://cyware.com/
About CSW
CSW is a cybersecurity services company focused on attack surface management and penetration testing as a service. Our innovation in vulnerability and exploit research led us to discover 45+ zero days in popular products such as Oracle, D-Link, WSO2, Thembay, Zoho, etc., among others. We became a CVE Numbering Authority to enable thousands of bug bounty hunters and play a critical role in the global effort of vulnerability management. As an acknowledged leader in Vulnerability research and analysis CSW is ahead of the game helping organizations world-wide to secure their business from ever-evolving threats. For more information visit www.cybersecurityworks.com or follow us on LinkedIn and Twitter.
View source version on businesswire.com: https://www.businesswire.com/news/home/20220126005014/en/
Contacts
Jenny Pfleiderer
Director, Corporate Communications
+1 925-878-5655
jenny.pfleiderer@ivanti.com













